Source - https://coinscapture.com/blog/what-is-cryptography
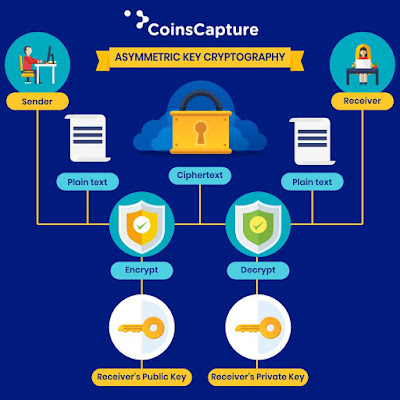
1. Asymmetric or Public key cryptography:
Nowadays, due to the increased number of cyber-crimes, it is necessary to safeguard all the corporate secrets, classified information, and personal information from any unauthorized access. This is the phase where Cryptography comes into play and helps you in securing all the important data and maintain its confidentiality. Here’s a blog to help you understand what is cryptography and how it safely transmits all the personal and financial data on the web in case of online purchase or transaction and smartly avoids any security breach.
Cryptography is a process of converting simple plain text into unreadable text with the help of codes which can be processed and read only by the individuals intended to do. The word "crypt" means "hidden" or "vault" and "graphy" means "writing." Through cryptography, data is not only protected from alteration or theft but also helps in user’s authentication. Let’s take the help of a scenario to get more familiar with cryptography.
Imagine two friends Daniel and Christin are chatting on a social platform. Daniel sends a message to Christin who is on the other side of the world. This message is supposed to be private and confidential, but unfortunately, there is a smart guy called Nick in between who got access to their social platform and was able to read all of their private chats. This can be very fatal. So, how could this problem be solved? That’s where cryptography helps.
Using cryptography, the readable text can be converted into an unreadable text by Daniel using a secret key to encrypt a message which is termed as a “Ciphertext”. Then Daniel sends this ciphertext over the social platform without any worry of anyone getting access to his message. Now, on the other side of the world, Christin would require the same secret key to decrypt this message in order to recover the original readable text. If anyone comes in between for eg. Nick, he won't be able to read the message because he lacks the decryption key.
Types of Cryptography: Based on the number of keys and algorithm, Cryptography is classified as:
1. Asymmetric or Public key cryptography:
The process in which two types of keys (public and private key) are required for encryption and decryption of the text. These keys are mathematically related to each other. Text can be encrypted with a public key and can be decrypted with the private key only. In order to avoid any security key breach, the private key has to be kept 100% secretly. The different types of asymmetric algorithms are RSA (Rivest-Sharmir-Adelman) algorithm is the most commonly used is this cryptography when sending sensitive data on the internet, Elliptic Curve Digital Signature Algorithm (ECDSA) is used byBitcoin, and Digital Signature Algorithm (DSA) is adopted as a Federal Information Processing Standard for digital signatures by NIST in FIPS 186-4.
2. Symmetric Cryptography:
The process in which only one key is required for encryption and decryption of the data. The sender uses this key to encrypt the plain text and send the ciphertext to the receiver. The receiver uses the same key and decrypt the ciphertext into plain text. The different types of symmetric algorithms are AES (Advanced Encryption Standard), DES (Data Encryption Standard), IDEA (International Data Encryption Algorithm), Blowfish (Drop-in replacement for DES or IDEA), RC4 (Rivest Cipher 4), RC5 (Rivest Cipher 5) and RC6 (Rivest Cipher 6)
3. Hash Functions:
In this process, there is no requirement of a key to encrypt or decrypt data. Instead, a fixed length of the hash value is computed by repeating/iterating the text randomly multiple times depending on the length of the plain text which makes the data impossible to recover. The different types of Hash functions are SHA-1 (Secure Hash Algorithm 1), SHA-2 and SHA-3.



Comments
Post a Comment